There is no silver bullet. Your strategy for defense cannot be singular. You must protect your organization on multiple fronts. Think of it as pillars supporting your company’s information security, those pillars being: security awareness training, policy, and risk assessments.
Information Security: What is The Silver Bullet?
Ransomware: A Modern Terror

Now that you know you can buy ransomware off the Dark Web for a couple of bucks, you understand the severity of the cyber risks if you don’t have the appropriate defense structures in place. Given that this threat is only expected to grow and evolve, staying aware of how cybercriminals acquire and release ransomware will help you avoid becoming a target on a day-to-day basis.
COMPANY POLICIES YOU SHOULD HAVE FOR SOCIAL MEDIA

The plain truth of the matter is that social media is absolutely necessary in this day and age. If you aren’t connected on at least one platform, you might as well not exist. People rely on your social media sites to find out about your business. So, how do you find the middle-ground between staying relevant and protecting yourself against the threat of releasing too much information? What policies can be enacted? What laws are out there to protect your interests?
Not Just Another Set of Rules: Cyber Policy

WHAT ARE CYBER SECURITY POLICIES?
Cyber security policies are a set of standards of care a company must have for working with information over a computer network. They ensure a company is operating in compliance with state and federal laws. Such policies are made up of lists of protocols and boundaries for employees to abide by, while working with computer systems.
Assess Your Investment: What Am I Getting Into With A Security Risk Assessment?
Why Do I Need Dark Web Monitoring?
A Deep Dive Into The Dark Web: How Do I Stay Protected?
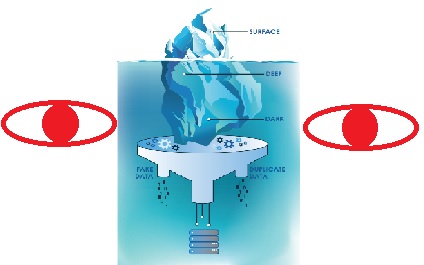
Whether it’s drugs, human trafficking, theft of intellectual property or personally identifiable information (PII), or any other criminal activity you can think of, the Dark Web is the playground of today’s cybercriminals. It is where any company, small or large, whose credentials have been compromised, will find them openly for sale to the highest bidder. And that person plans to use them against you.
Phishing on Social Media: A Case Study in Scamming

When you hear about phishing scams, you might picture someone falling for a Nigerian prince scheme they get sent over email or possibly the robocalls you tend to get during tax season. But did you know that such scams are also being conducted by cybercriminals over nearly all social media platforms?
PHISHING: HOW DO I TELL A MESSAGE OR EMAIL IS UNTRUSTWORTHY?
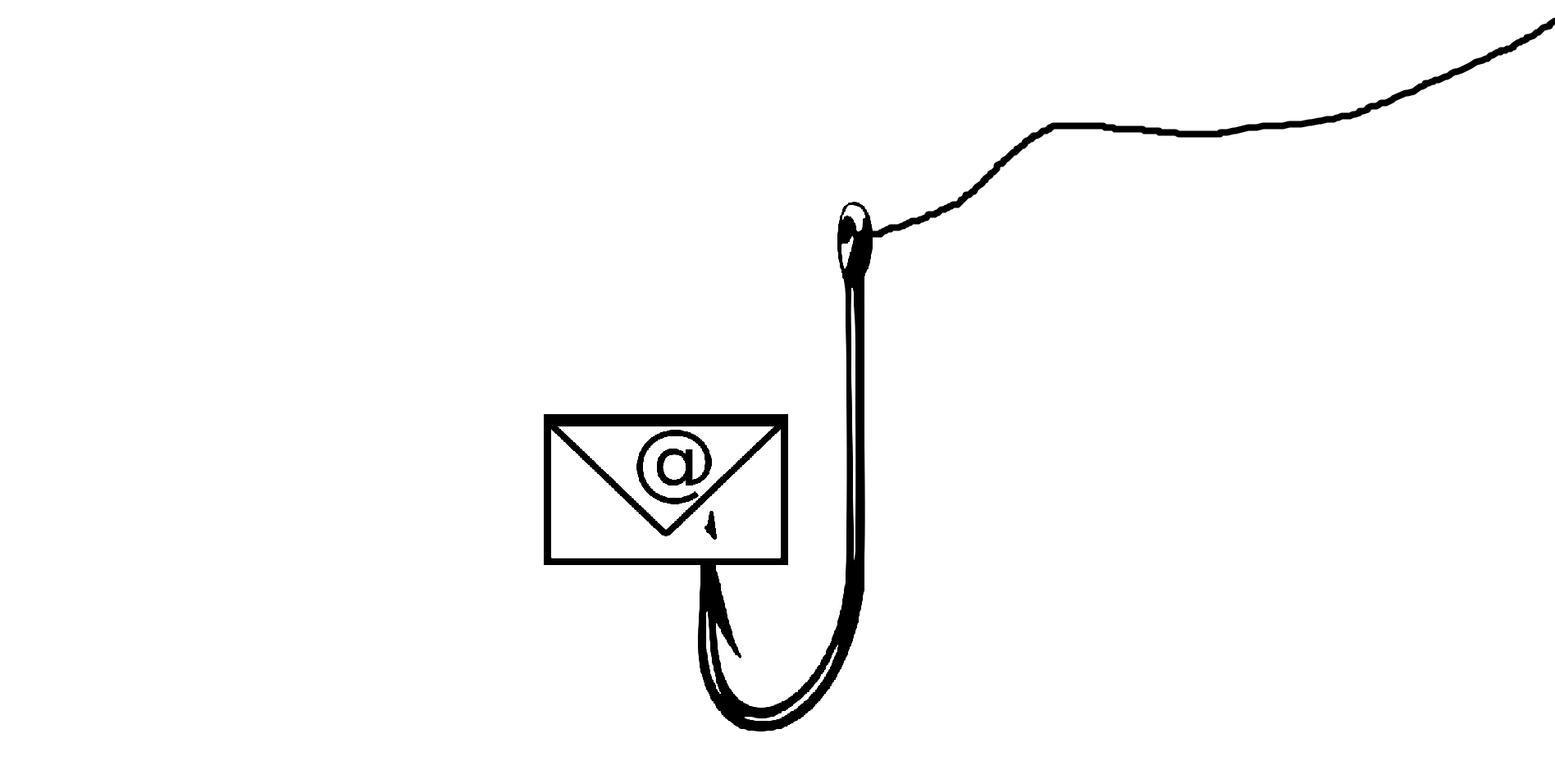
Ever heard of Phishing? It’s any type of attack where a cybercriminal steals your private information by tricking you or somebody else into giving it to them. These attacks are often conducted through spam email that you click on or through theft of your account information, through accessing your pages.
Train Before Tragedy: Are You Security Aware?
- 1
- 2




